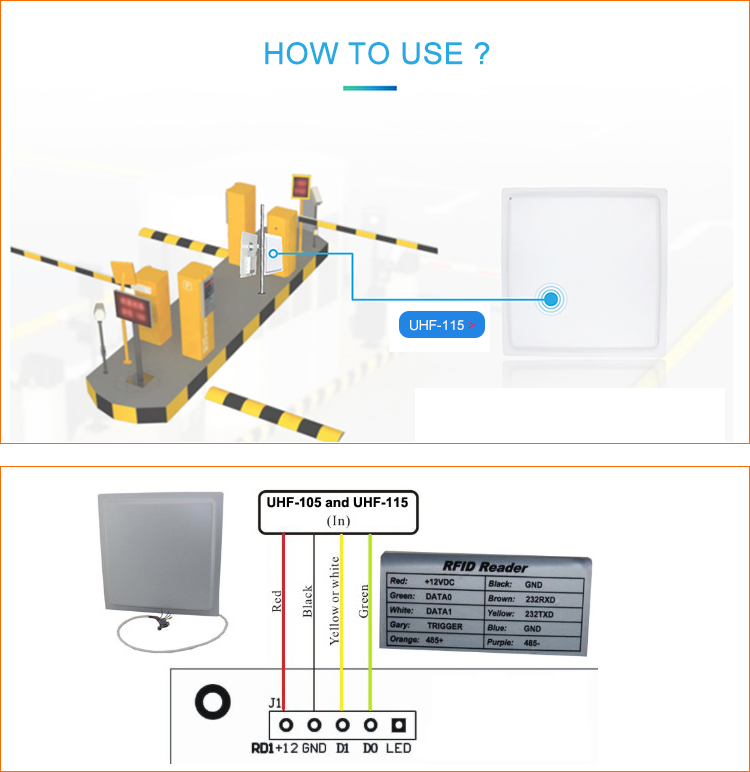
What's the UHF Card Read Range and Working Performance?
The 25 meters UHF rfid reader range and working performance of UHF parking card readers can vary depending on the specific model and manufacturer. These characteristics are key factors in determining the effectiveness of the access control system. Here are general considerations related to UHF card read range and working
Performance:
Read Range:
10dbi UHF RFID antenna typically offer a read range that can extend from a few feet to several meters. The exact range depends on factors such as the reader's design, antenna configuration, and environmental conditions.
Adjustability:
Some RFID card UHF provide adjustable read ranges, allowing system administrators to customize the distance at which the card is detected. This flexibility is useful for tailoring the system to the specific requirements of a parking facility.
Environment and Interference:
The working performance of UHF card readers can be influenced by the environment. Quality readers are designed to function reliably in various conditions, including outdoor settings and locations with potential electronic interference.
Consistency:
Customers seek UHF card readers that deliver consistent performance across different situations. Consistency is crucial for ensuring that access control operations, such as gate opening or barrier lifting, occur reliably and without delays.
Speed of Reading:
The speed at which UHF card readers can process and authenticate card information is an important aspect of working performance. Faster reading speeds contribute to the efficiency of access control processes.
Reliability:
Reliable working performance is a fundamental expectation. Users want assurance that UHF card readers consistently and accurately read card information, minimizing instances of false positives or failures to authenticate.
Compatibility with Card Technology:
UHF card readers should be compatible with the UHF RFID technology used in parking cards. This ensures seamless communication between the card and the reader, optimizing the overall working performance of the access control system.
For precise information on the UHF card read range and working performance of a specific model, it is recommended to refer to the product documentation provided by the manufacturer. This documentation typically includes technical specifications, performance metrics, and guidelines for optimal use.
Author: Written by Ms.Anna Zhang from S4A INDUSTRIAL CO., LIMITED